FrostGuard is freezing us out with its hacks...
Incident Response
Tags: Linux CLI Splunk JQ CloudTrail Logs S3 Access Logs
Scenario Our IT Team have an urgent need for the analysis of a set of S3 Access logs and some corresponding CloudTrail data. We think some data may have leaked after a mistake in a configuration change. FrostGuard needs you...

This investigation machine provides with 2 AWS related logs which are AWS CloudTrail and S3 Access log (treat it like webserver access log but for S3 storage).
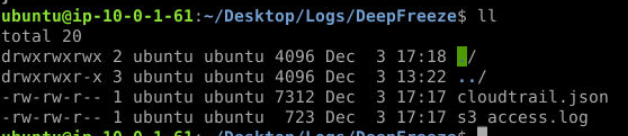
After taking a look at file size of both files, we would not need tool like Splunk to query efficiently but if you still want to use Splunk then you could the next section for Splunk preparation.

This investigation room tagged with "Linux CLI", "Splunk" and "JQ" beside CyberChef we found on Desktop, lets find them to confirm its presence
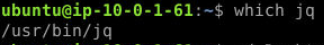
First, we can easily find the existence of jq by simply using which jq command that will print out where the binary of jq located on this machine and it is indeed installed on this machine

At the bottom of the screen, we can see that Sublime Text was also installed on this machine

Then after open Mozilla Firefox browser, we can see that there is a quick tab to Splunk running on port 8000
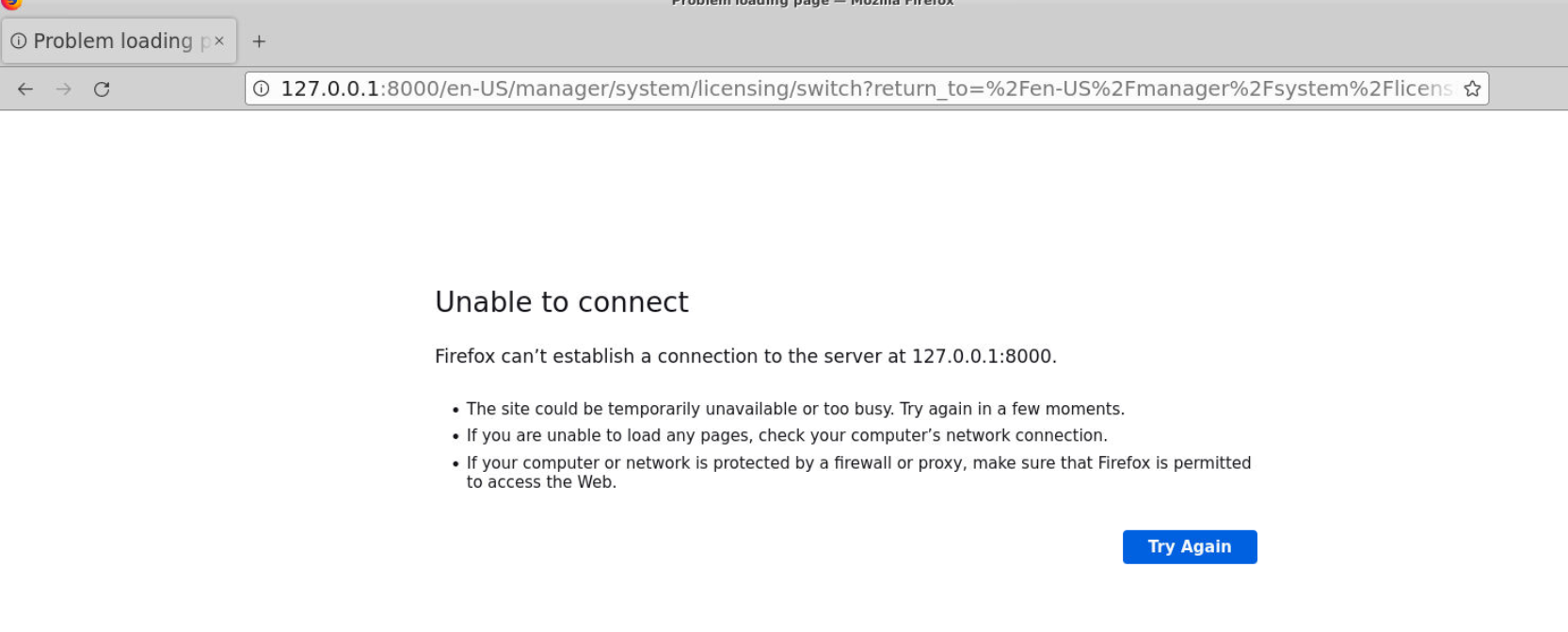
But we are unable to connect so we will have to manually start Splunk via its binary on this system
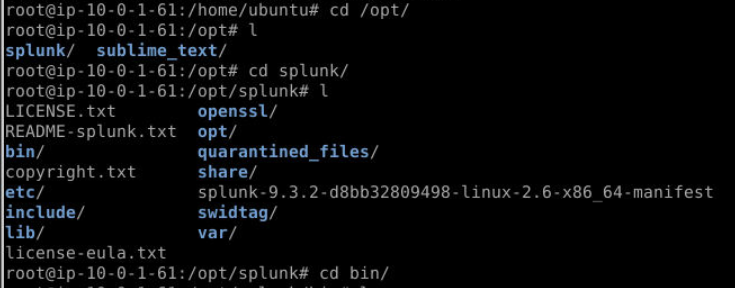
Splunk is located at /opt/splunk, we will have to execute splunk binary inside /opt/splunk/bin directory.
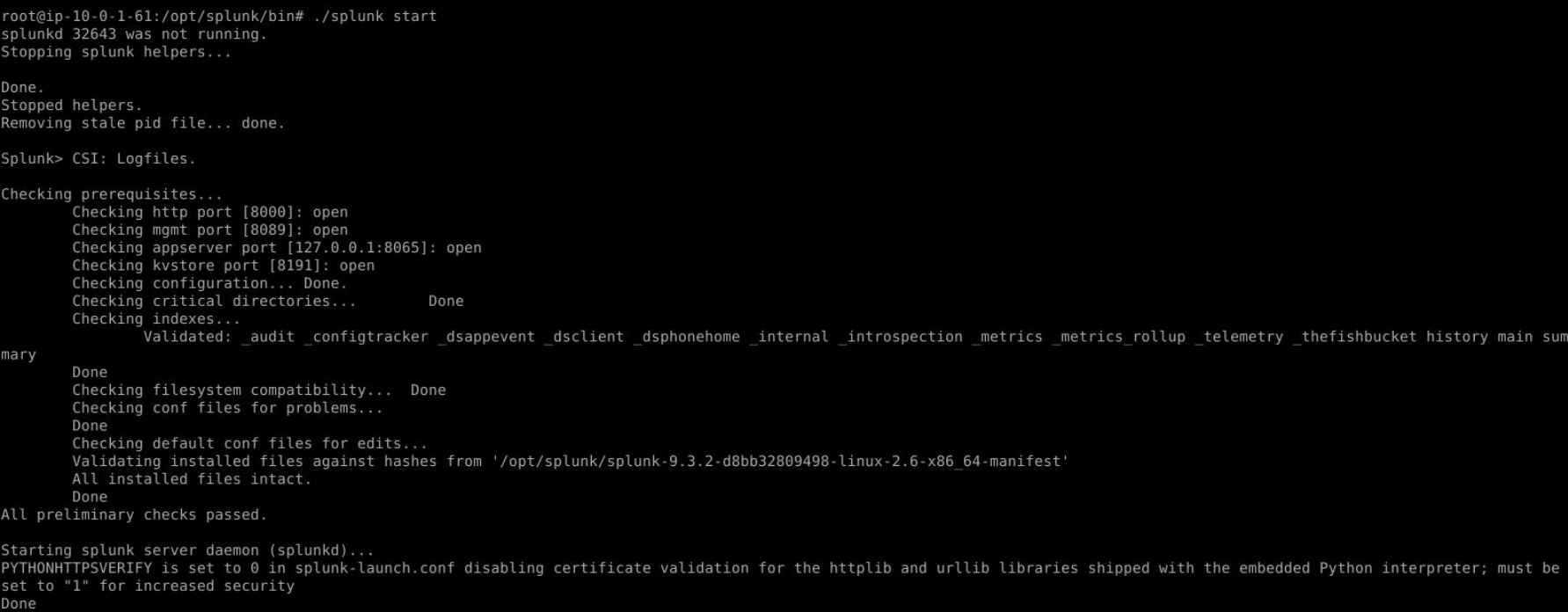
Execute the command : /opt/splunk/bin/splunk start and wait for a sec until Splunk web interface is ready.
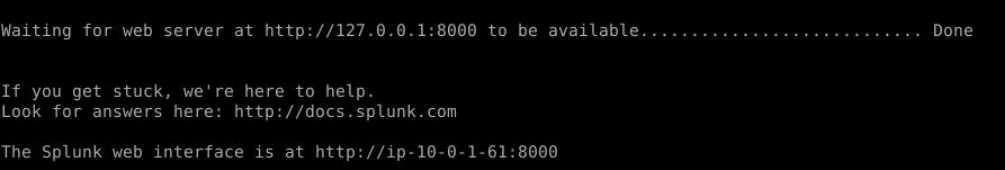
Splunk will tell user that its web interface is ready like this so we can go back to refresh Splunk web interface on Firefox or just accessed it with this new URL.
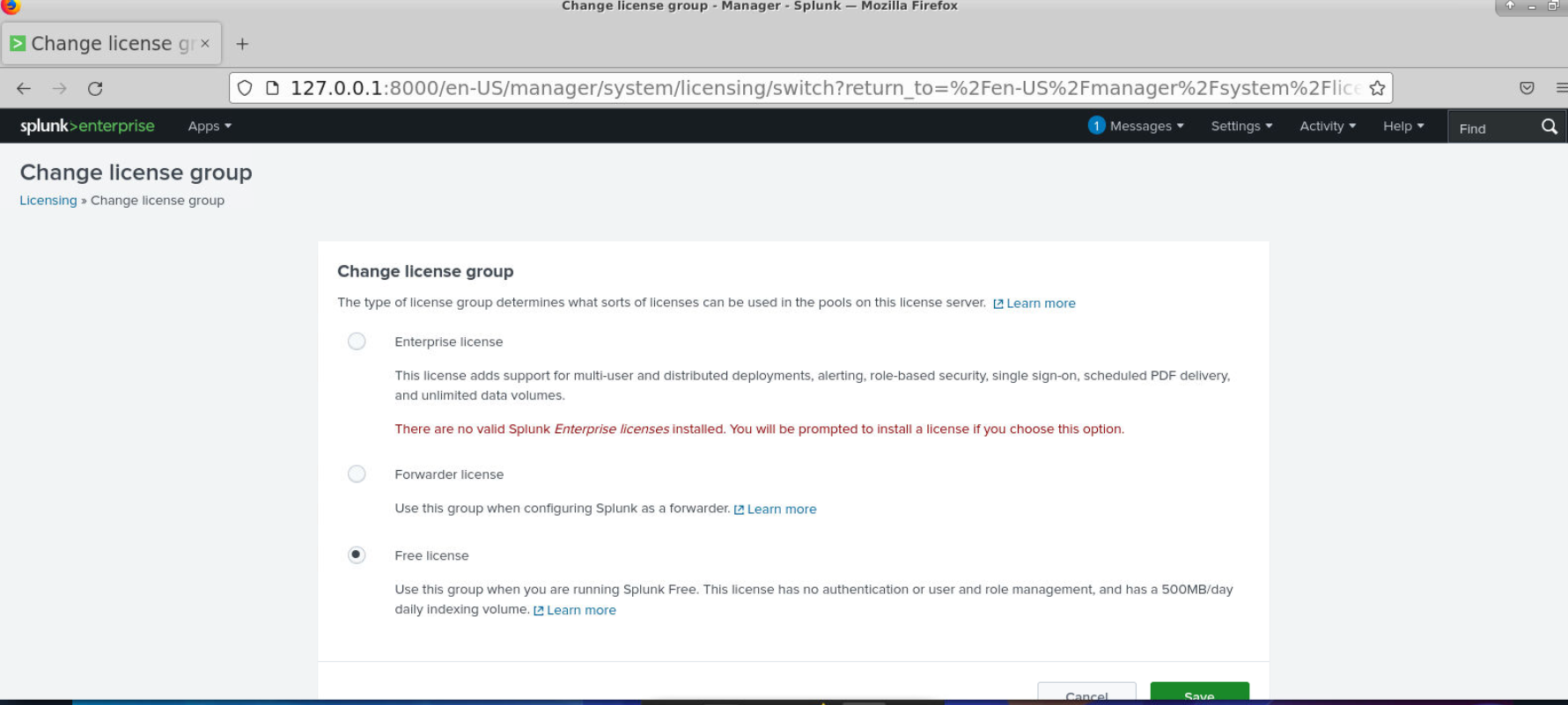
Change license group page will appear as soon as it finished loading but do not worry, just click "Save" button as we can use Free license to query our log.
Splunk restart will be required so we can just click "Restart Now" and wait for a sec before browse to index page.
Now what we need to do is to import our log into Splunk.
Go to http://127.0.0.1:8000/en-US/manager/search/adddata to upload files.
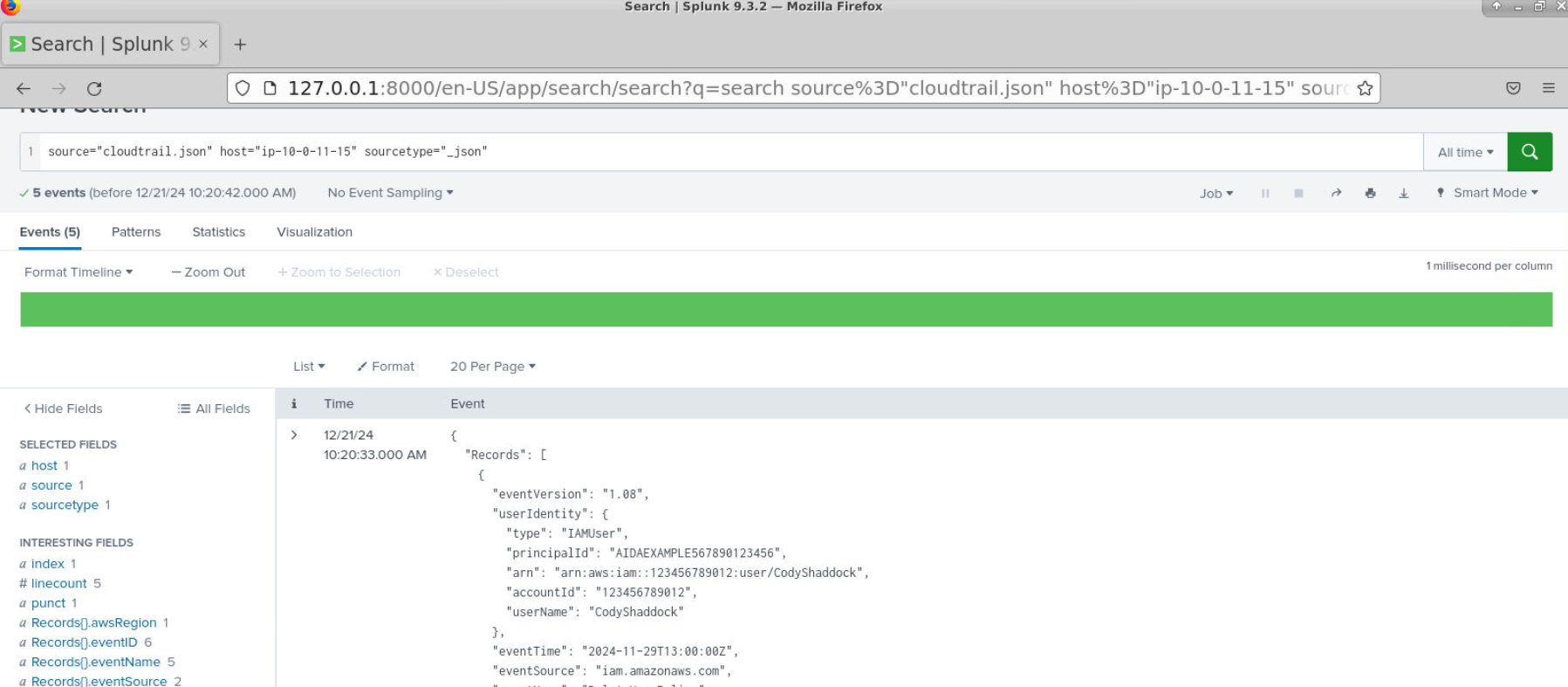
Now you are ready for the investigation using Splunk. (which I didn't use btw)
Q1) The IT team accidentally applied an overly permissive policy to the subject’s AWS user account, instead of a specific policy. What policy was applied, and what is the username of the subject? (Format: Username, PolicyName)
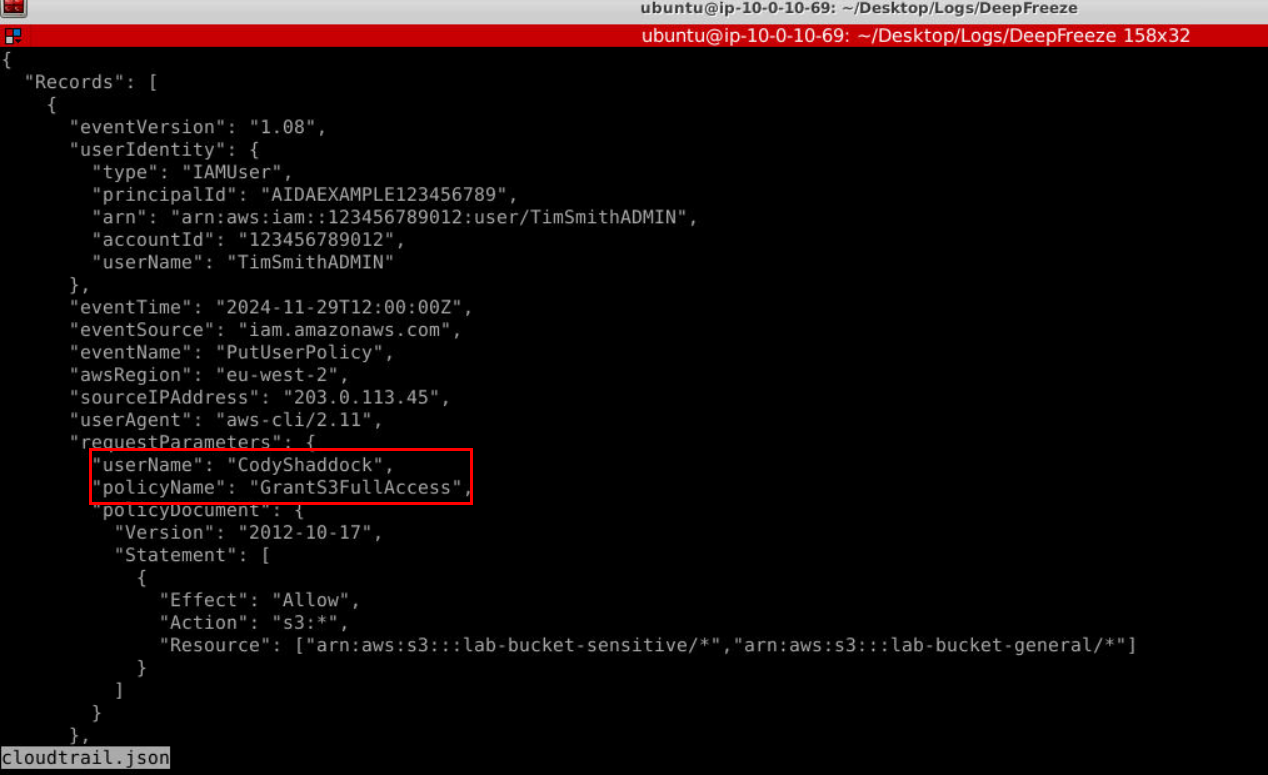
Lets start with AWS CloudTrail and The first even we will see is PutUserPolicy event and as it names imply, its an event that will add or update a policy to IAM user and this record showed that username "CodyShaddock" was added with GrantS3FullAccess policy which will provides full access to all S3 buckets via AWS Management Console so this is overly permissive policy that we are looking for.
Answer
CodyShaddock, GrantS3FullAccessQ2) What is the username of the account that made this change? (Format: Username)
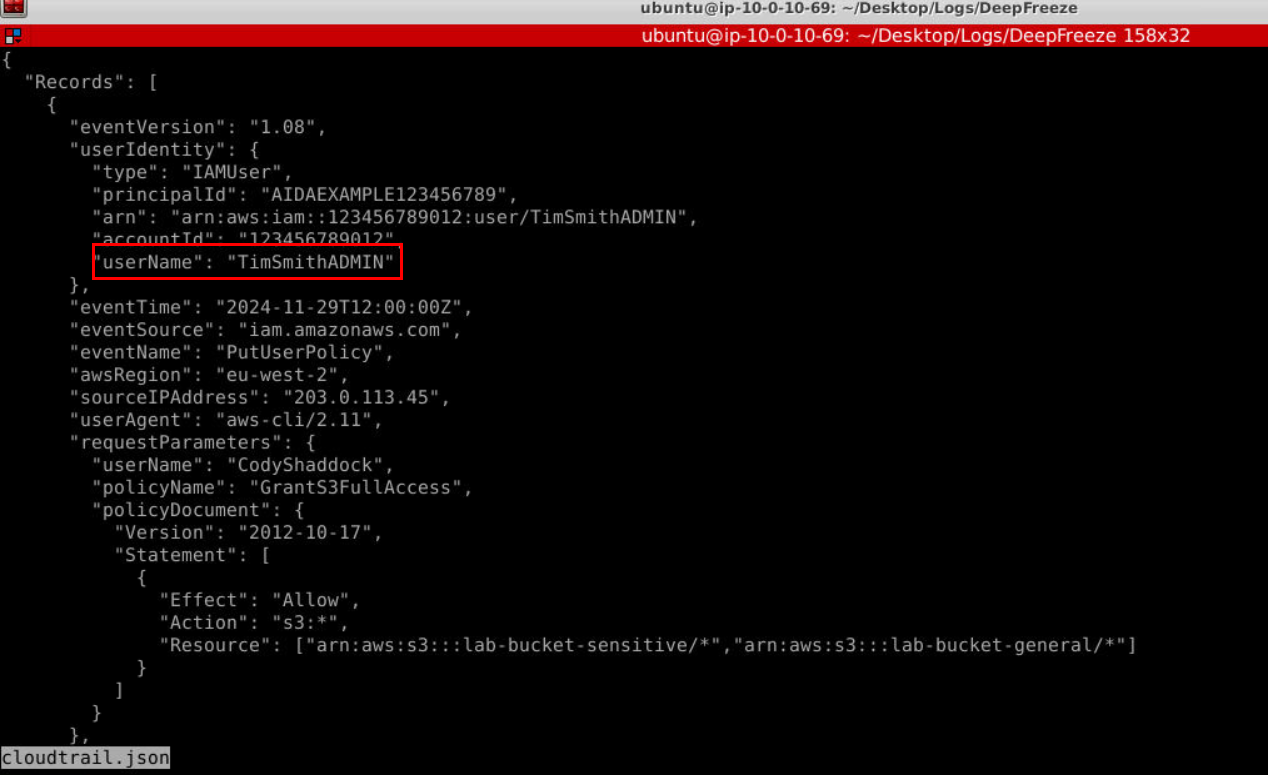
The user responsible for this action is "TimSmithADMIN"
Answer
TimSmithADMINQ3) What S3 buckets were made available to the subject? (Format: Bucket1, Bucket2)
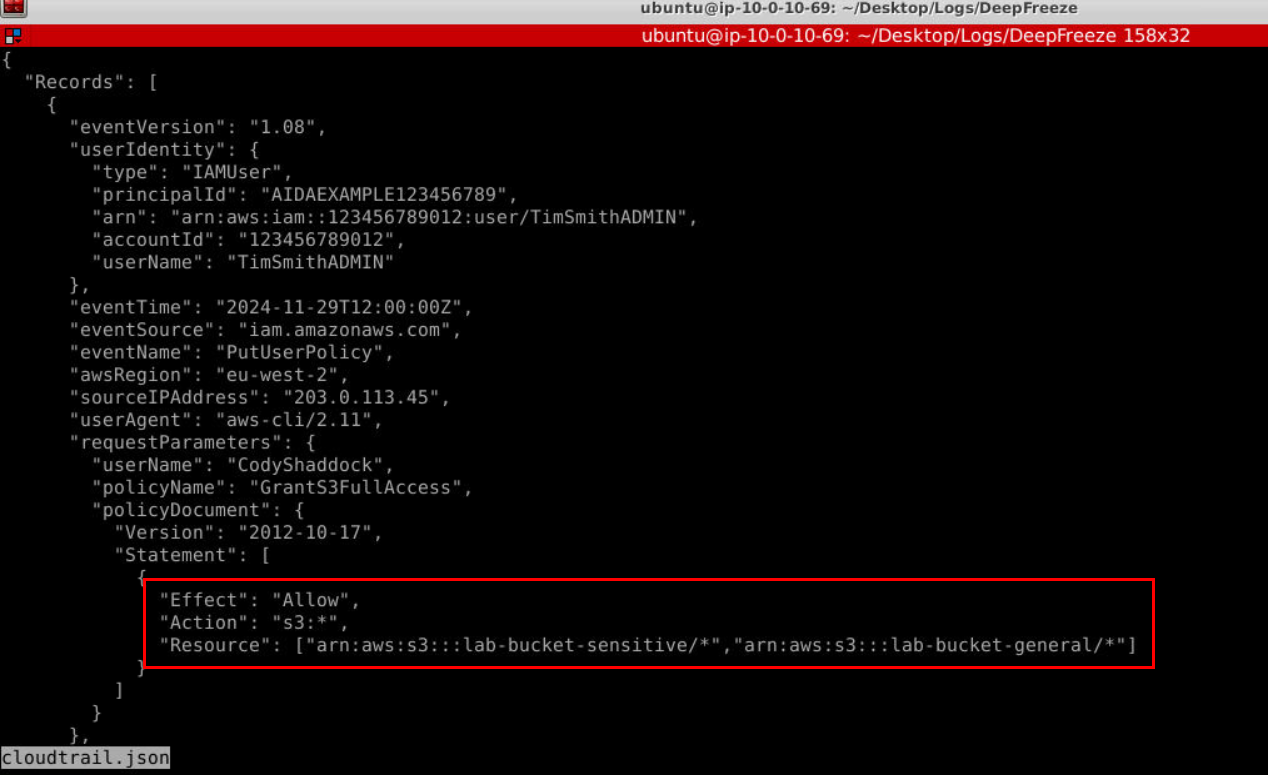
Under "Statement" section, we can see these 2 S3 buckets were made available due to new policy added to "CodyShaddock"
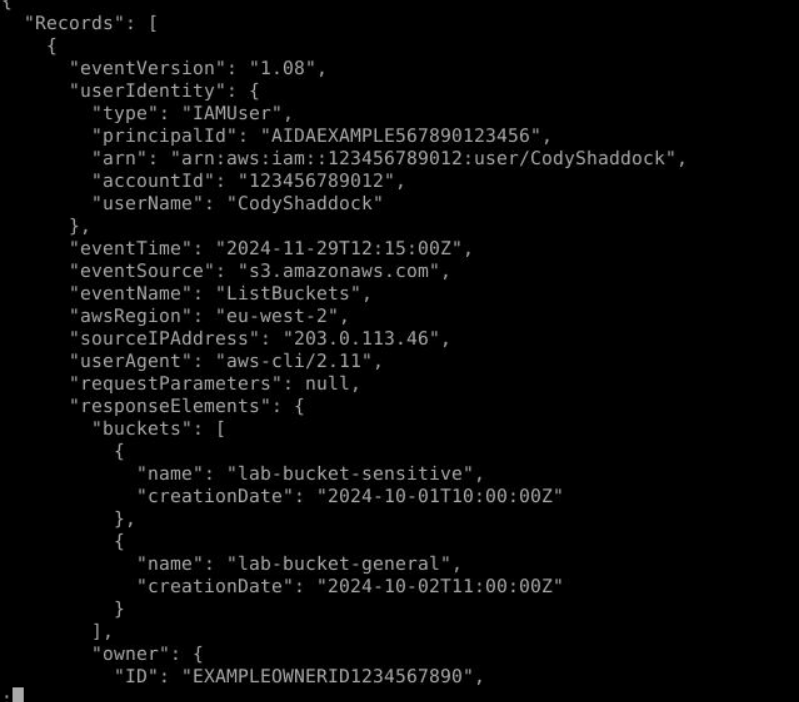
We can also confirm this with record below that which is ListBuckets event that will return all available S3 buckets to authenticated request sender.
Answer
lab-bucket-sensitive, lab-bucket-generalQ4) What is the Insider Threat Matrix preparation section ID most relevant to this activity? (Format: PRXXX)
GrantS3FullAccess is a policy that will increase privilege for specific user which match PR024: Increase Privileges on Insider Threat Matrix.
Answer
PR024Q5) What IP address did the subject use when enumerating the S3 buckets, and what event name is present? (Format: X.X.X.X, EventName)
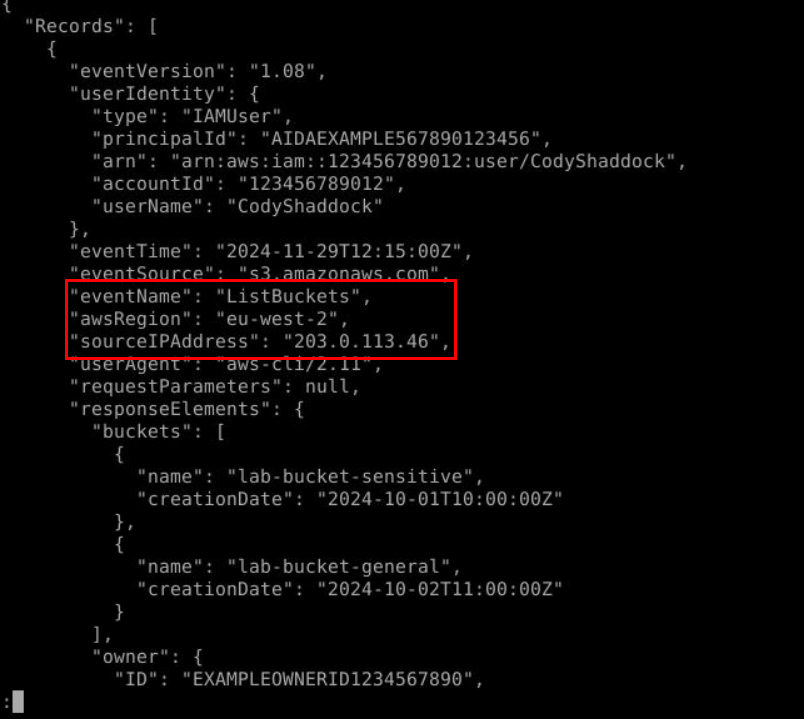
We know which event can be used to retrieve available S3 buckets so we will just have to grab source IP Address of this request right here.
Answer
203.0.113.46, ListBucketsQ6) What type of retrieval was used, and what is the event name? (Format: xxxx, EventName)
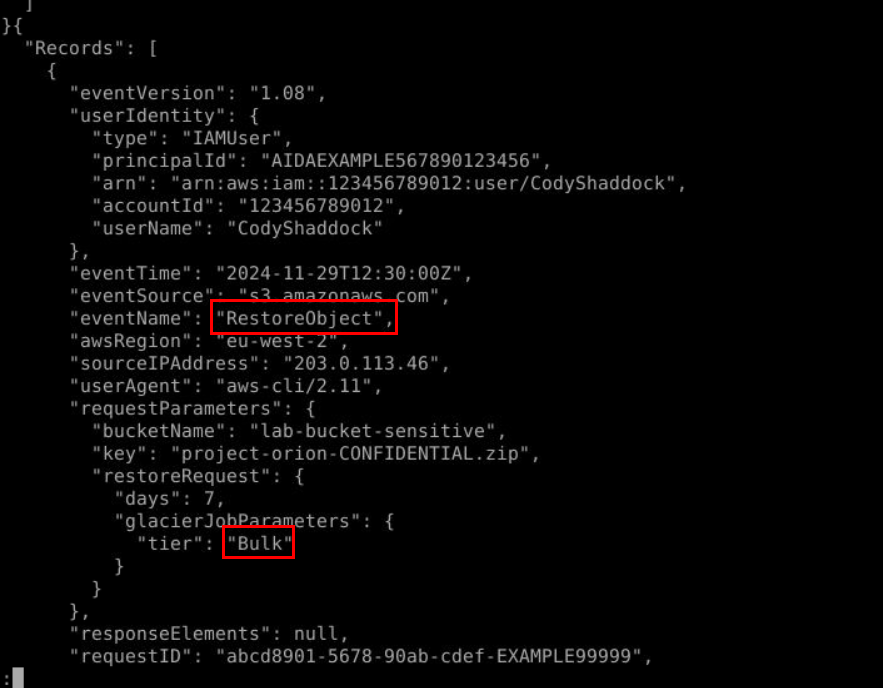
After listing S3 storages, next event we will see is RestoreObject which is an event to create a temporary of the object from S3 Glacier archive storage which can be downloaded or accessed and the retrieval tier is "When restoring an object, you can choose how quickly you need the data" which will range from
| Tier | Time to Retrieve | Cost | Use Case |
|---|---|---|---|
| Expedited | 1–5 minutes | Highest cost | Urgent small data retrieval. |
| Standard | 3–5 hours | Moderate cost | Regular access with reasonable speed. |
| Bulk | 5–12 hours (Glacier), 48 hours (Deep Archive) | Lowest cost | Large-scale, non-urgent data recovery. |
Then we can see that retrieval tier on this event is "Bulk"
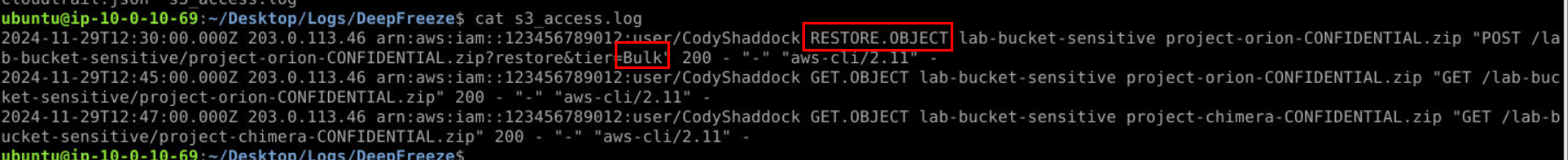
We can also found this request on S3 access log right here.
Answer
bulk, RestoreObjectQ7) What bucket was targeted in the retrieval request? (Format: BucketName)
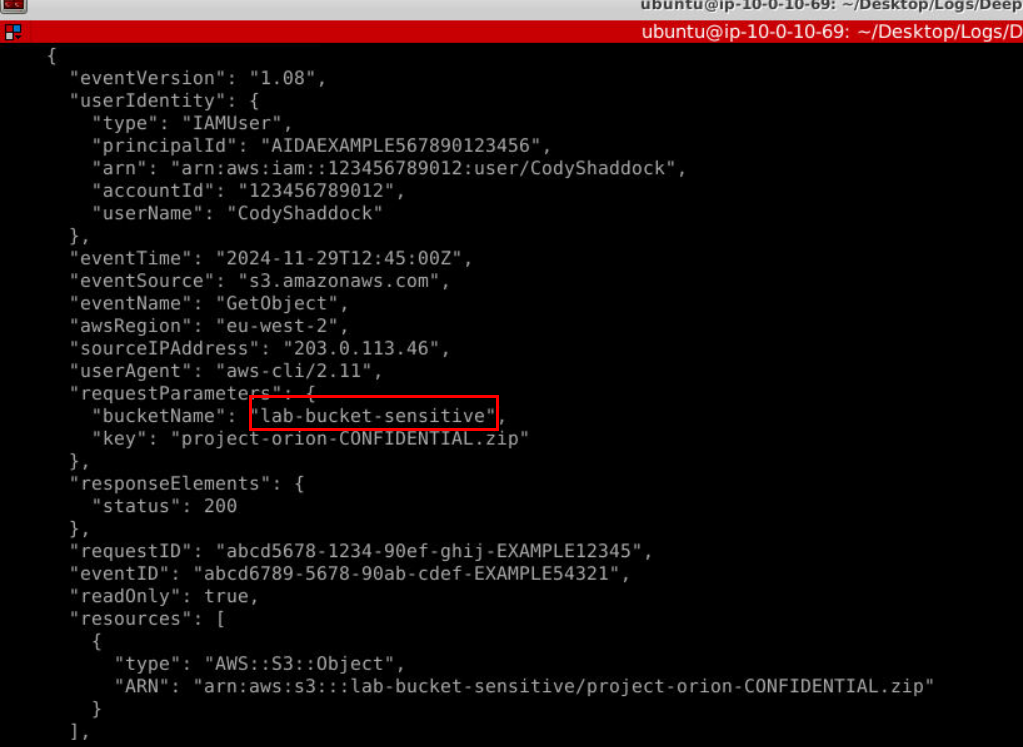
After RestoreObject event, 2 GetObject were made to download zip files from S3 buckets and those files reside in this sensitive bucket.
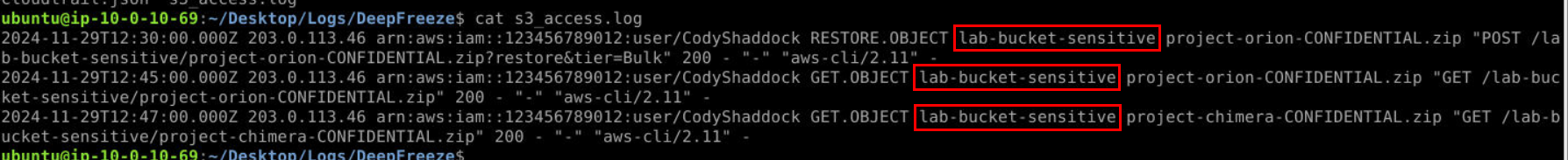
From S3 Access Log, we can see that all 3 requests were made to specifically for this bucket.
Answer
lab-bucket-sensitiveQ8) What is the timestamp of the retrieval request? (Format: YYYY-MM-DDTHH:MM:SS)
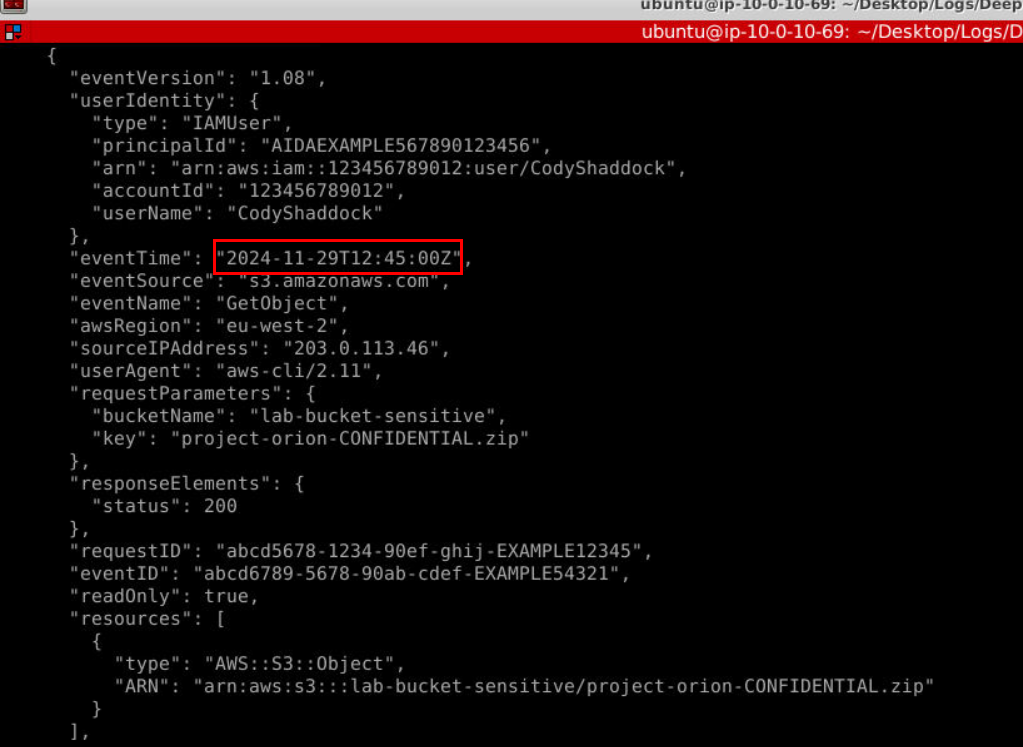
There are 2 GetObject events, the timestamp I submitted is the first GetObject event right here.
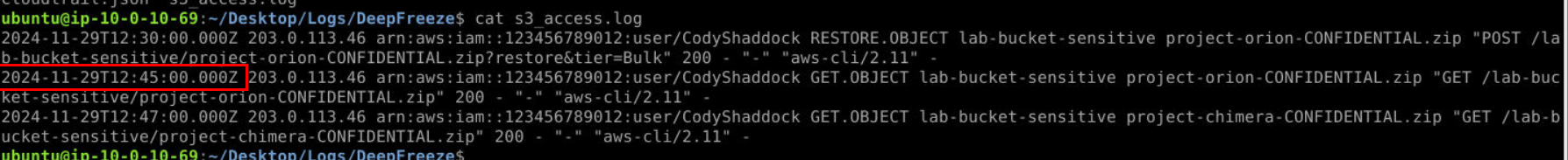
Which can also be retrieve from S3 Access Log right here.
Answer
2024-11-29T12:45:00Q9) What are the names of the files downloaded by the subject? (Format: file1.ext, file2.ext)
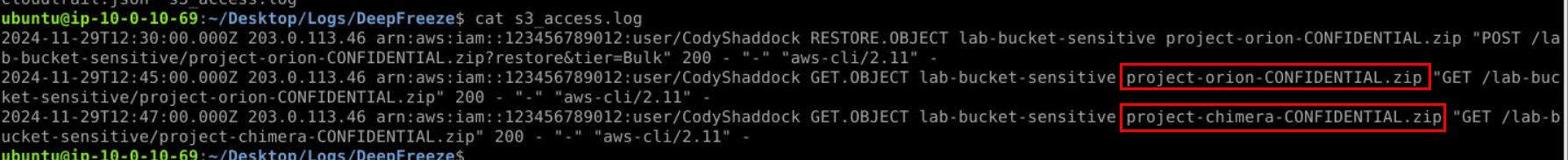
We can obtain the names of both files from CloudTrail or S3 Access Log right here.
Answer
project-orion-CONFIDENTIAL.zip, project-chimera-CONFIDENTIAL.zipQ10) What is the Insider Threat Matrix preparation section ID most relevant to this activity? (Format: PRXXX)
We know that GetObject request were made to download sensitive files which match PR-025: File Download from Insider Threat Matrix
Answer
PR025Q11) What policy was removed from the subject’s user account, and what is the event name? (Format: PolicyName, EventName)
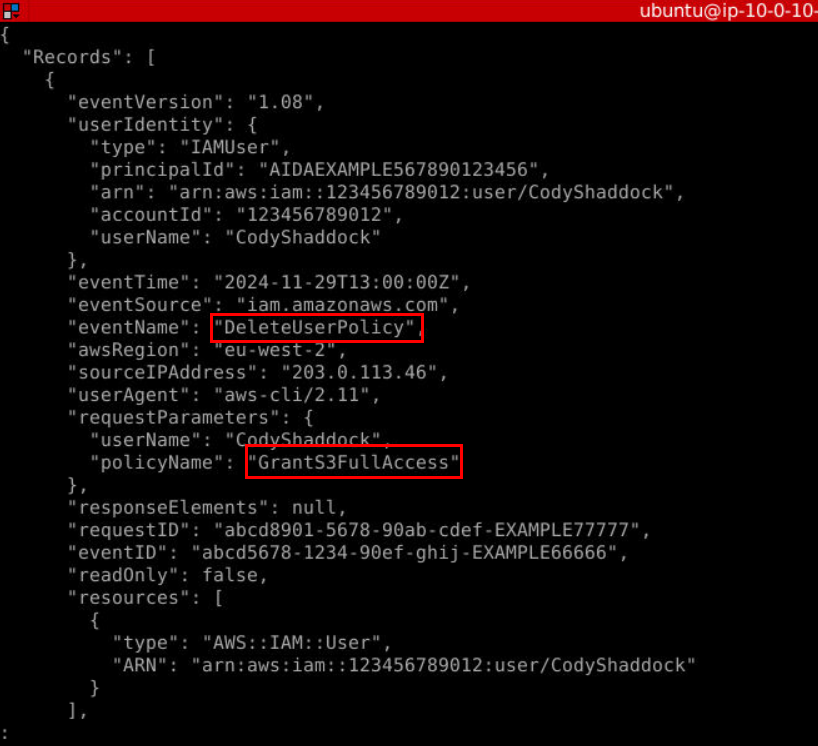
We can see on the last record on CloudTrail that GrantS3FullAccess Policy was deleted from "CodyShaddock" by DeleteUserPolicy event.
Answer
GrantS3FullAccess, DeleteUserPolicyQ12) What is the Insider Threat Matrix anti-forensics section ID most relevant to this activity? (Format: AFXXX)
Which will decrease privilege of that user back before it was granted with full S3 access.
Answer
AF019 https://blueteamlabs.online/achievement/share/52929/249
https://blueteamlabs.online/achievement/share/52929/249
After "TimSmithADMIN" (IT team) applied "GrantS3FullAccess" policy to "CodyShaddock" user which made then started to restore object within "lab-bucket-sensitive" bucket from S3 Glacier Deep Archive and exfiltrated 2 confidential files from the bucket then remove "GrantS3FullAccess" from "CodyShaddock" user.
project-orion-CONFIDENTIAL.zip object from "lab-bucket-sensitive" bucket203[.]0[.]113[.]46